Připravíme pro vás od jednoduché web prezentace, přes eshop, po profi web s administrací téměř cokoliv.
Vymyslíme a naprogramujeme internetový online systém na přání. Nakódujeme vám API i speciální požadavky.
Vyrobíme aplikaci pro mobilní zařízení dle vašeho přání a zadání. Android, iPhone, Windows phone.
Zajistíme pro vás webhosting, virtuální server, zaregistrujeme domény, postaráme se o emaily, databáze, DNS.
Poradíme vám v oblasti optimalizací pro vyhledávače (SEO, ASO), s optimalizací webu i stránek aplikací.
Umíme navrhnout také logo, vizitky, banner. Provozujeme Open source systémy (Wordpress, Drupal...)
Realizace posledních prací.

Prodejna potravin a smíšeného zboží v Klimkovicích.

Internetové stránky houslařského ateliéru s nabídkou služeb a eshopem.
Databáze deskových a společenských her.
Informace o českých podcastech
Internetové stránky a motivační kalendář.
Internetové stránky odborného učilistě v Hlučíně. Kompletní správa.
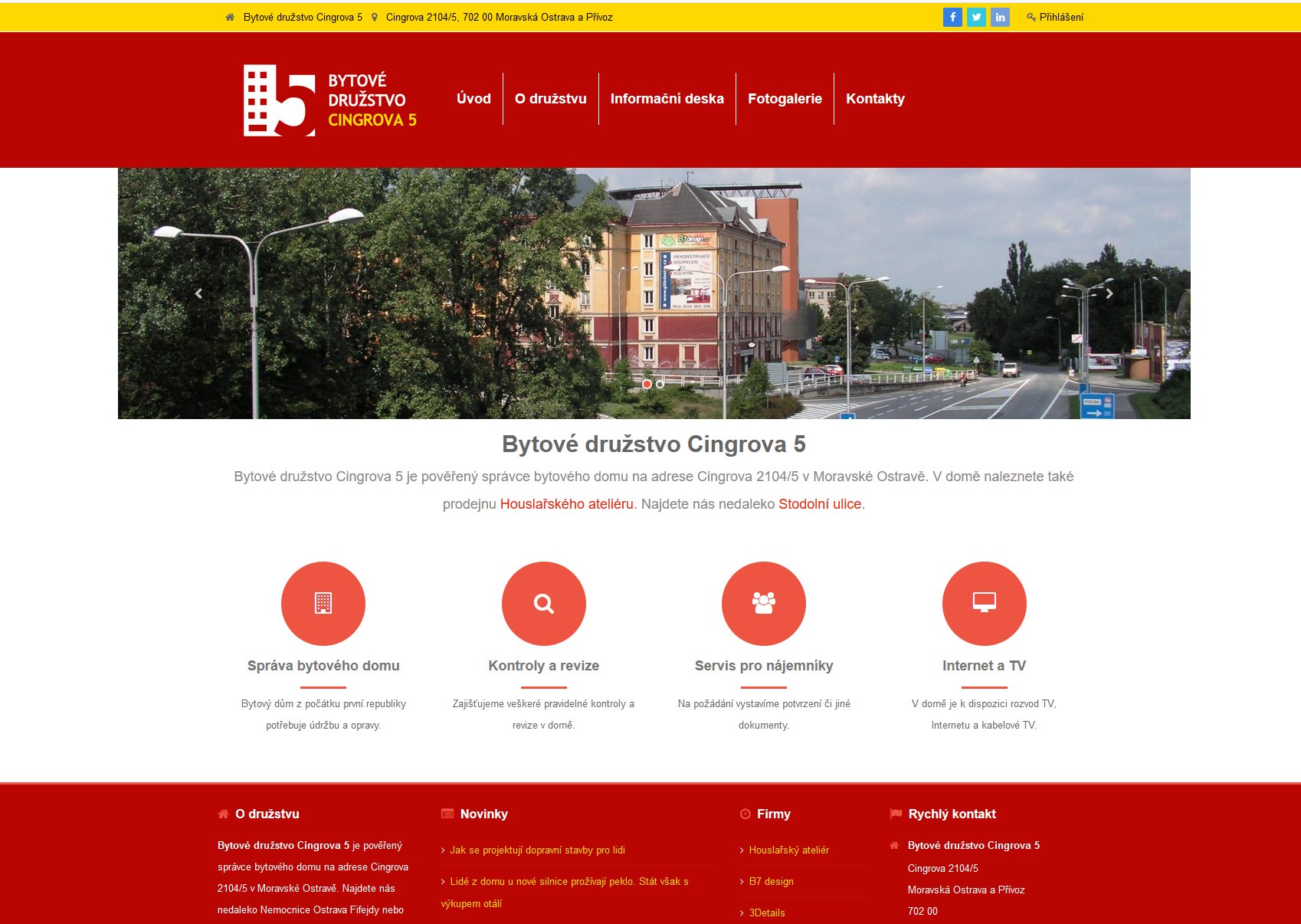
Internetové stránky bytového družstva s administrací nástěnky.
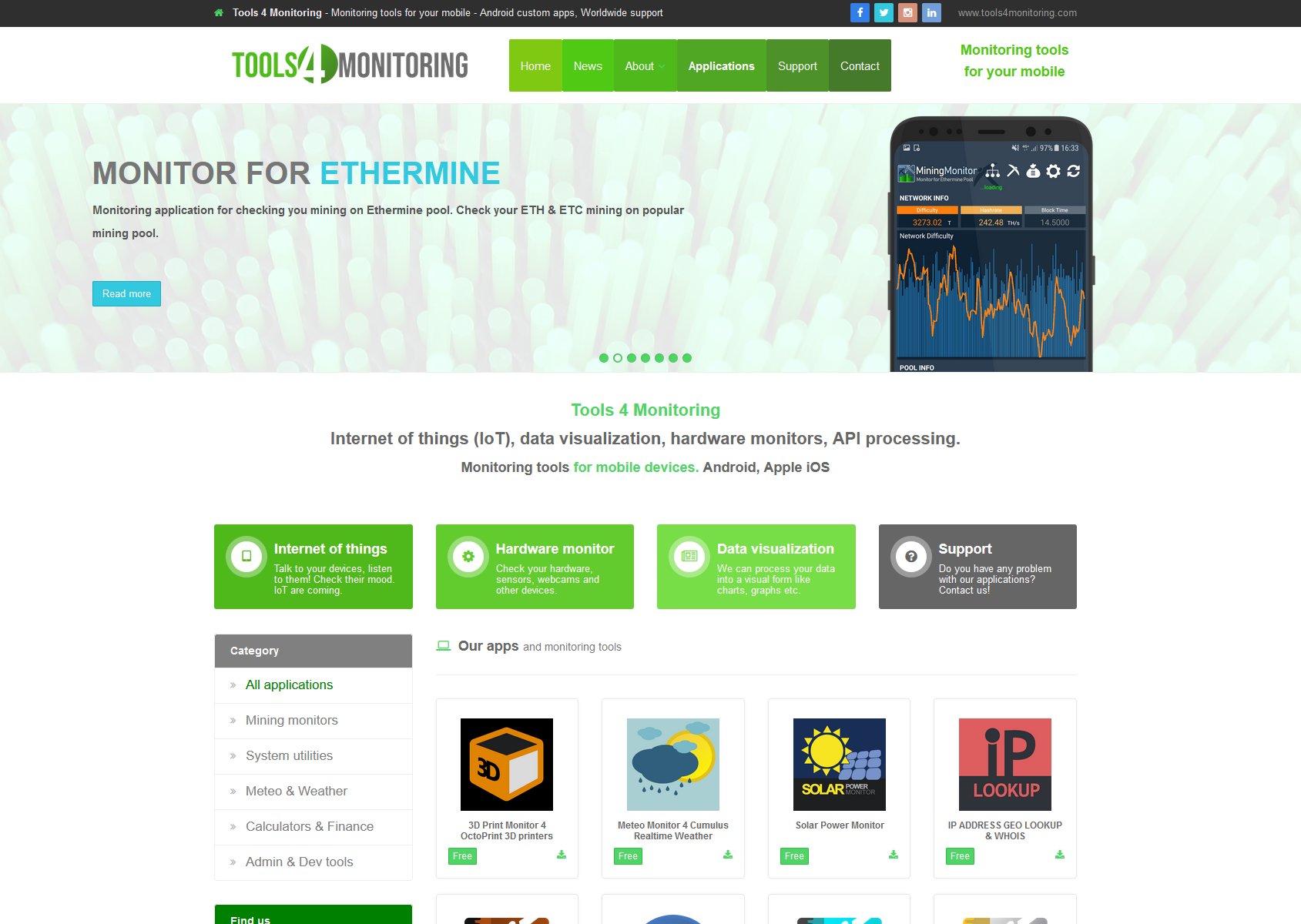
Intenetové stránky vývojáře aplikací pro Android a iOS.
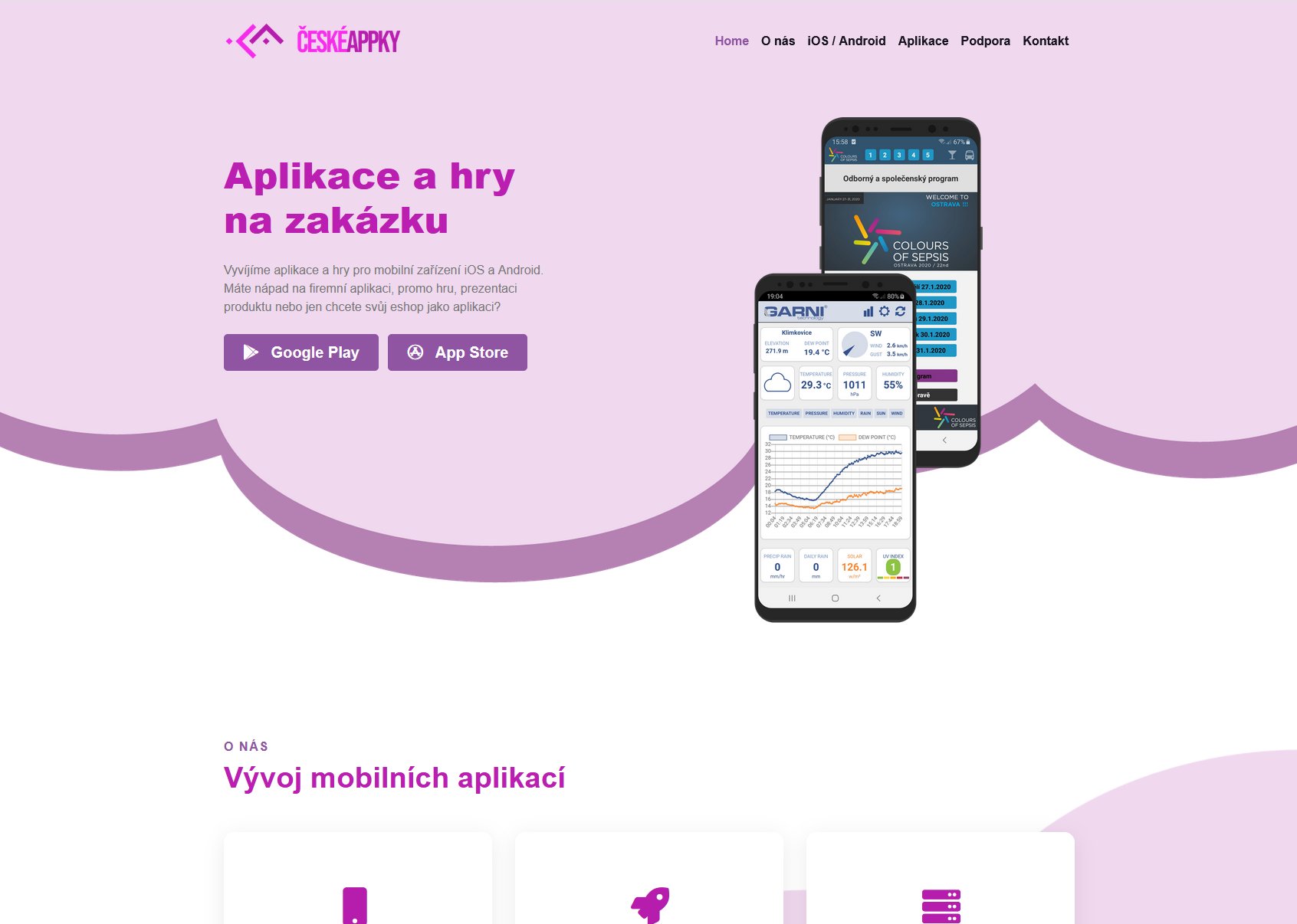
Český vývojář mobilních aplikací pro Android a iOS. Oficiální aplikace Garni, Colours of Sepsis, akutně.cz a dalších
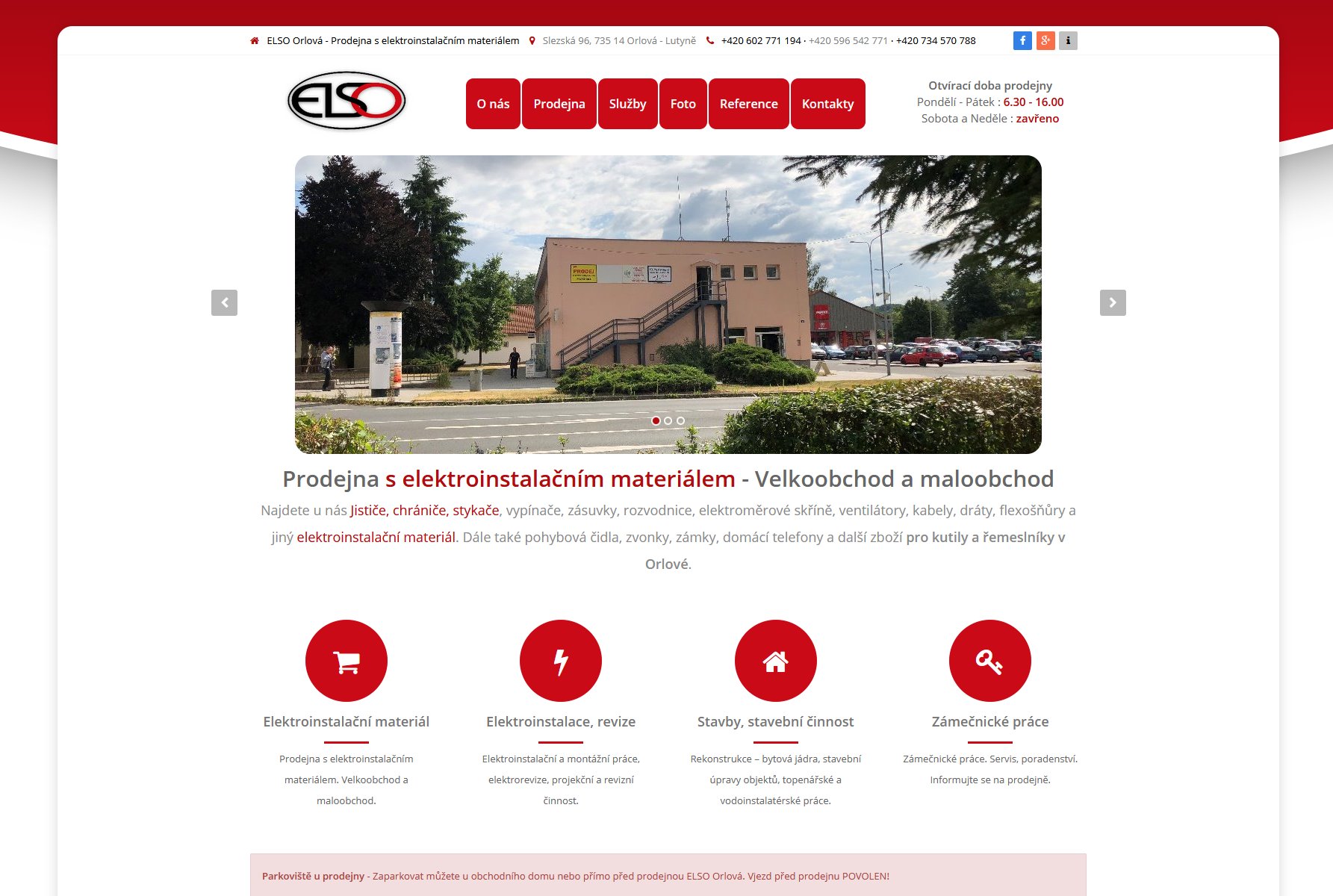
Oficiální stránky společnosti ELSO Orlová.

www stránky eshopu s ochrannými pracovními pomůckami.
Vývojář her pro windows, android a ios

Poslední internetové novinky a zajímavosti ze světa IT.